Are you confident your personal information is safe online? Every day, new threats in cybersecurity put your data, money, and privacy at risk.
These issues aren’t just technical problems—they affect your life directly. Understanding the challenges hackers use and the gaps in security can help you protect yourself better. Keep reading to uncover the hidden dangers lurking in the digital world and learn what you can do to stay one step ahead.

Credit: www.columbiasouthern.edu
Common Cyber Threats
Cybersecurity faces many challenges that affect individuals and businesses. Common cyber threats target sensitive data and disrupt services. Knowing these threats helps protect your information and devices. Below are some of the most frequent cyber threats today.
Malware And Ransomware
Malware is software designed to harm or exploit systems. It includes viruses, worms, and trojans. Ransomware is a type of malware that locks files. Attackers demand payment to restore access. These threats can cause data loss and financial damage.
Phishing Attacks
Phishing tricks users into giving personal information. Attackers use fake emails or websites. They appear real but steal passwords and credit card details. Phishing is common and often hard to spot. It targets both individuals and companies.
Insider Threats
Insider threats come from people within an organization. Employees or partners may misuse access to data. Sometimes it is accidental, other times intentional. These threats are difficult to detect. They can lead to serious data breaches.
Ddos Attacks
Distributed Denial of Service (DDoS) attacks overload servers. They flood a website with traffic to make it crash. This stops users from accessing services. DDoS attacks can damage a company’s reputation. They require strong defenses to prevent disruptions.
Zero-day Exploits
Zero-day exploits take advantage of unknown software flaws. Developers have not yet fixed these bugs. Hackers use them to gain unauthorized access. These exploits are dangerous because they are hard to defend against. Quick updates and patches are crucial.
Impact On Businesses
Cybersecurity issues hit businesses hard. The effects go beyond just technology. They impact finances, trust, daily work, and legal standing. Every business, big or small, feels these impacts deeply.
Financial Losses
Cyber attacks often lead to big money losses. Theft of data can cause direct financial damage. Fixing security breaches costs a lot too. Lost sales happen when customers stop trusting a business. All these add up and hurt profits.
Reputation Damage
Trust is key for any business. A security breach can damage a company’s good name. Customers may stop buying or sharing their information. Negative news spreads fast online. Recovering a damaged reputation takes time and effort.
Operational Disruptions
Cyber threats can stop daily business activities. Systems may go offline or slow down. Employees cannot work properly without access to data. This causes delays and missed deadlines. Operations become chaotic and less efficient.
Legal And Compliance Risks
Many countries have strict data laws. Failure to protect information can lead to lawsuits. Companies may face fines or penalties. Compliance with regulations is essential to avoid trouble. Legal problems drain resources and focus from growth.
Vulnerable Targets
Cybersecurity faces many challenges due to vulnerable targets. These targets attract attackers because of weak defenses or high value. Understanding these targets helps protect data and systems better. Various sectors struggle with different security risks. Each target type requires special attention and strategies.
Small And Medium Enterprises
Small and medium enterprises (SMEs) often lack strong security tools. They may not afford expert staff or advanced software. Attackers see them as easy marks for data theft. Many SMEs use outdated systems or weak passwords. These gaps make them vulnerable to ransomware and phishing.
Critical Infrastructure
Critical infrastructure includes power plants, water systems, and transport networks. These systems are essential for daily life and safety. Cyberattacks here can cause serious damage and chaos. Many infrastructures run on old technology with little protection. Securing these targets is vital to prevent large-scale disruptions.
Cloud Services
Cloud services store huge amounts of data for businesses and users. Misconfigurations or weak access controls expose sensitive information. Attackers exploit these mistakes to steal or delete data. Cloud providers and clients must work together to ensure strong security. Regular updates and audits reduce risks significantly.
Iot Devices
Internet of Things (IoT) devices include smart home gadgets and wearables. Many have poor security settings and weak encryption. Hackers can use them to enter larger networks or spy on users. The rapid growth of IoT increases the attack surface. Securing these devices is essential for personal and network safety.
Preventive Measures
Preventive measures form the backbone of strong cybersecurity. They help stop threats before damage occurs. Each step taken reduces risk and protects data. Simple actions can save companies from costly breaches.
Employee Training
Employees are the first line of defense. Teaching them about phishing and safe internet use cuts risks. Regular training updates keep everyone alert to new threats. A well-informed team acts quickly to avoid mistakes.
Strong Authentication
Strong authentication means using more than just passwords. Two-factor authentication adds an extra security layer. It requires a code or fingerprint along with a password. This process makes it harder for hackers to break in.
Regular Software Updates
Software updates fix security holes found in programs. Running the latest version protects devices from attacks. Ignoring updates leaves systems vulnerable to hackers. Set devices to update automatically for best protection.
Network Segmentation
Network segmentation divides a network into smaller parts. It limits how far hackers can move inside. If one segment is breached, others stay safe. This tactic helps contain threats and protect sensitive data.
Advanced Security Solutions
Advanced security solutions help protect data from growing cyber threats. These tools use smart technology to find and stop attacks fast. They improve how companies defend their systems every day.
These solutions combine different methods to secure networks, devices, and information. They reduce risks and make it harder for hackers to succeed.
Ai And Machine Learning
AI and machine learning detect threats by learning from data patterns. They spot unusual behavior that shows an attack early. These technologies adapt over time to new risks.
They help security teams work faster and make better decisions. AI can analyze large data sets that humans cannot handle quickly.
Threat Intelligence Platforms
Threat intelligence platforms collect and share information about cyber threats. They provide real-time data on attack methods and sources. This helps organizations prepare and respond to attacks.
These platforms connect many sources to give a broad view of the threat landscape. They support better planning and stronger defense strategies.
Endpoint Detection And Response
Endpoint detection and response (EDR) tools monitor devices like laptops and phones. They watch for signs of attacks and respond immediately. EDR helps stop threats before they spread.
These tools give detailed information about attacks to help fix problems fast. They keep endpoints secure, a common target for hackers.
Zero Trust Architecture
Zero trust architecture means never trusting any user or device by default. It requires strict verification before access to resources is allowed. This reduces the chance of unauthorized access.
It limits user permissions to only what is needed. This approach helps contain breaches and protect sensitive data.
Credit: clarusway.com
Future Cybersecurity Trends
Cybersecurity is changing fast. New technology brings new risks and solutions. Staying ahead means knowing what trends shape the future.
Experts watch several key areas. These trends affect how we protect data and systems. Understanding them helps prepare for upcoming challenges.
Quantum Computing Challenges
Quantum computers can break many current security methods. They solve problems that are hard for normal computers. This power threatens encryption that keeps data safe. Cybersecurity experts must create new defenses that resist quantum attacks.
Increased Automation
Automation helps detect and respond to threats faster. Machines can scan millions of events in seconds. Automated tools reduce human error and speed up fixes. Yet, attackers also use automation to launch attacks quickly. Balance is needed to use automation well in defense.
Privacy-enhancing Technologies
Protecting user privacy grows more important. New tools help keep personal data safe while using services. Techniques like encryption and data masking hide sensitive information. These technologies build trust and meet stricter privacy rules.
Regulatory Changes
Governments introduce tougher cybersecurity laws worldwide. Companies must follow rules about data protection and breach reporting. Non-compliance leads to heavy fines and damage to reputation. Staying updated on laws is essential for all businesses.
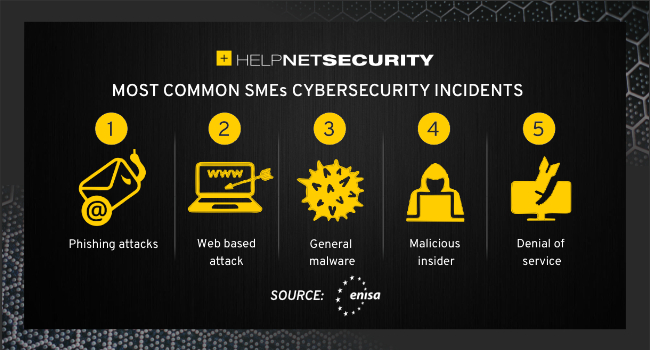
Credit: www.helpnetsecurity.com
Frequently Asked Questions
What Are The Biggest Cybersecurity Issues Today?
The biggest cybersecurity issues include phishing attacks, ransomware, data breaches, and insider threats. These threats exploit vulnerabilities in systems and human behavior. Businesses and individuals must stay vigilant and update security measures regularly to prevent costly damages and data loss.
How Do Cyber Attacks Impact Businesses?
Cyber attacks can cause financial loss, reputational damage, and operational disruption. They may lead to stolen sensitive data and legal penalties. Businesses must implement strong security protocols and employee training to minimize risks and ensure business continuity in a cyber-threat landscape.
Why Is Employee Training Important In Cybersecurity?
Employee training reduces risks caused by human error, such as falling for phishing scams. Educated employees recognize threats and follow security best practices. Regular training enhances overall cybersecurity defense and helps organizations stay compliant with regulations.
What Role Does Software Vulnerability Play In Cybersecurity?
Software vulnerabilities are flaws hackers exploit to gain unauthorized access. Regular software updates and patching fix these weaknesses. Addressing vulnerabilities promptly protects systems from attacks and minimizes the chance of data breaches.
Conclusion
Cybersecurity challenges grow as technology advances fast. Threats like hacking and data theft affect everyone. Staying aware and cautious helps protect personal and business information. Strong passwords and software updates reduce risks. Education and teamwork improve security for all users.
Everyone plays a role in keeping data safe. Taking small steps now avoids bigger problems later. Security is a shared responsibility we must take seriously.





