Imagine waking up to find your computer running slower than usual, your device heating up unexpectedly, or your internet suddenly crawling. What if these signs mean someone is secretly using your device to mine cryptocurrency without your knowledge?
This hidden danger is called cryptojacking, and it’s a growing cybersecurity threat that could affect you right now. Understanding how cryptojacking works and how to protect yourself is crucial—because if you don’t act, your personal data, device performance, and even your digital security could be at serious risk.
Keep reading to discover what cryptojacking is, how to spot it, and most importantly, how to defend your devices from this silent cyber attacker.

Credit: kratikal.com
What Is Cryptojacking
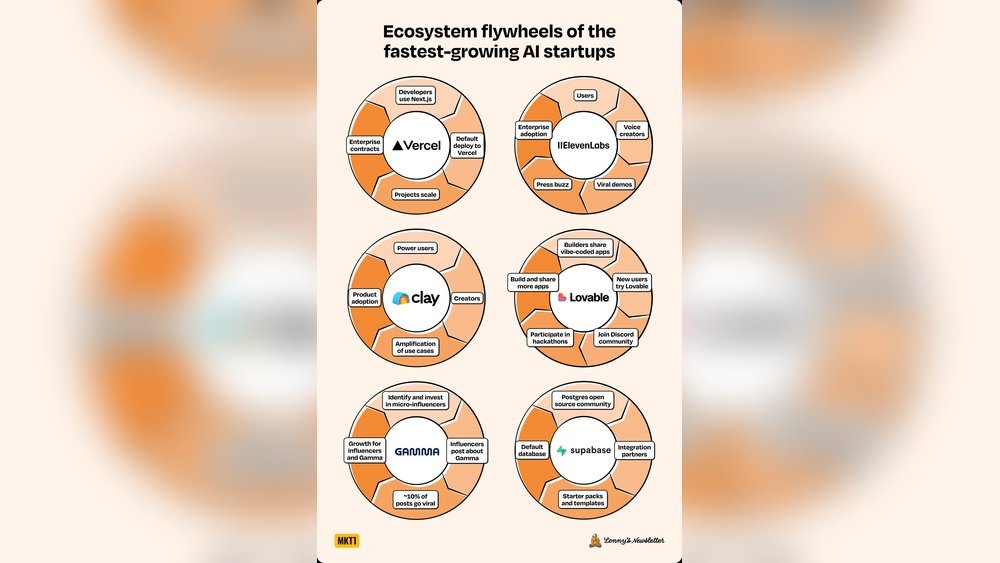
Cryptojacking is a hidden cyber threat that affects computers and devices worldwide. It happens when hackers secretly use your device to mine cryptocurrency. This means your device works harder without your permission. You might not notice anything unusual at first. But over time, your device may slow down or overheat. Cryptojacking steals your resources and can cause real damage.
How Cryptojacking Works
Hackers install special software on your device. This software runs in the background. It uses your computer’s power to mine digital coins. Mining needs a lot of processing power. Your device’s CPU or GPU does the heavy work. You do not get any benefit from this mining. All the rewards go to the attacker. The software often hides well and avoids detection. This allows it to run for a long time unnoticed.
Common Cryptojacking Techniques
One popular method is through malicious websites. Visiting these sites can start mining without your knowledge. Another way is through infected apps or software downloads. Hackers can also send emails with harmful links or attachments. These tricks install cryptojacking scripts on your device. Some attackers use browser extensions to mine cryptocurrency. These techniques all have one goal: use your device’s power secretly.
Signs Of Cryptojacking
Cryptojacking is a hidden cyber threat that uses your device to mine cryptocurrency. It often goes unnoticed but leaves clear signs. Detecting these signs early can protect your data and device health. Here are some common signs of cryptojacking to watch for.
Device Performance Issues
Your device may slow down without clear reason. Programs may freeze or take longer to open. The battery may drain faster than usual. Your device might heat up even when idle. These problems often signal cryptojacking malware using your device’s power.
Unusual Network Activity
Look for strange data usage spikes. Your internet speed might drop suddenly. Unknown connections or processes could appear in your network logs. Cryptojacking software often sends data to remote servers. This unusual network activity helps cybercriminals mine cryptocurrency secretly.
Risks To Digital Assets
Cryptojacking poses serious risks to your digital assets. It steals computing power to mine cryptocurrency without consent. This stealthy threat can lead to various damaging effects. Understanding these risks helps protect your data and finances.
Financial Implications
Cryptojacking increases electricity bills due to heavy computer use. It slows down devices, reducing work efficiency and productivity. Repairing damaged systems adds unexpected costs. Businesses may face lost revenue from interrupted services. These financial impacts can accumulate fast.
Data Security Concerns
Cryptojacking often involves malware that can steal sensitive information. It weakens system security, making data vulnerable to other attacks. Personal and business data risks exposure or theft. Recovery from data breaches requires time and resources. Protecting data is critical to avoid these dangers.

Credit: gbhackers.com
Preventing Cryptojacking Attacks
Preventing cryptojacking attacks is vital for protecting your devices and data. These attacks use your computer’s power to mine cryptocurrency without permission. They slow down your system and increase energy costs. Taking steps to stop cryptojacking can keep your devices safe and running smoothly.
Use Of Security Software
Security software helps detect and block cryptojacking scripts. Antivirus programs scan files and websites for threats. Some tools specialize in blocking mining scripts in real time. Keeping such software active adds a strong layer of defense.
Regular Software Updates
Updating software closes security gaps hackers exploit. Many cryptojacking attacks use outdated systems as entry points. Install updates for your operating system, browsers, and apps promptly. Automatic updates make this process easier and more reliable.
Safe Browsing Habits
Avoid suspicious websites that may host cryptojacking scripts. Do not click on unknown links or pop-ups. Use browser extensions that block mining scripts. Careful browsing reduces the chance of accidental infections.
Responding To Cryptojacking
Responding to cryptojacking swiftly is key to protecting your devices and data. This type of cyberattack hijacks your system’s resources to mine cryptocurrency without your consent. Understanding how to detect and remove cryptojacking threats can reduce damage and restore normal device function.
Identifying Infected Devices
Watch for unusual slowdowns and high CPU usage. Cryptojacking often causes devices to overheat and work harder than usual. Check your device’s performance and battery life closely. Unexplained spikes in network activity may also signal an infection. Use trusted security tools to scan for hidden threats. Early detection helps stop cryptojacking before it spreads.
Removing Malicious Scripts
Malicious scripts run cryptojacking code in browsers or apps. Clear your browser cache and disable unknown extensions. Update software and operating systems to patch vulnerabilities. Run a full antivirus scan to find and delete harmful files. In some cases, resetting your device may be necessary. Regular maintenance keeps your systems safe from future attacks.
Future Of Cryptojacking
The future of cryptojacking poses new challenges for cybersecurity. Attackers keep finding clever ways to mine cryptocurrency without permission. This threat evolves quickly, forcing security teams to adapt fast.
Understanding future trends helps businesses and individuals stay safe. New cryptojacking methods may target devices beyond computers. Smartphones, IoT gadgets, and cloud servers are at risk.
Emerging Threat Trends
Cryptojackers use more stealthy techniques to avoid detection. They hide mining scripts inside apps or websites. Some attacks run only when devices are idle.
Attackers may combine cryptojacking with other cyber threats. For example, they might steal data while mining coins. This makes attacks harder to spot and stop.
More cryptojacking may shift to mobile devices and smart gadgets. These devices often have weaker security controls. This creates new opportunities for cybercriminals.
Advancements In Protection
Security experts develop better tools to detect mining activity fast. Machine learning helps identify unusual patterns in device behavior. This improves early warning systems.
Browser extensions and antivirus software now block cryptojacking scripts. These tools protect users without slowing down their devices.
Stronger device security and regular software updates reduce risks. Training users to spot suspicious signs also helps. Awareness is key in stopping cryptojacking attacks.

Credit: cyble.com
Frequently Asked Questions
What Is Cryptojacking In Cybersecurity?
Cryptojacking is unauthorized use of your device to mine cryptocurrency. Hackers use malware or scripts to exploit your system’s resources without consent.
How Can I Detect Cryptojacking On My Device?
Look for slow performance, overheating, and high CPU usage. Check for unknown processes and unusual network activity regularly.
What Are Common Cryptojacking Attack Methods?
Attackers use malicious email links, infected websites, and compromised ads. They also embed mining scripts in software or browser extensions.
How To Prevent Cryptojacking Attacks Effectively?
Keep software updated, use strong antivirus, and block suspicious sites. Avoid clicking unknown links and disable unnecessary browser extensions.
Conclusion
Cryptojacking is a hidden threat that affects many devices today. It steals computer power without your knowledge. Protect your system with strong passwords and updated software. Watch for unusual slowdowns or overheating. Stay alert to keep your data and devices safe.
Regular checks help catch problems early. Cybersecurity matters for everyone using the internet. Don’t let cryptojackers take control of your technology. Simple steps can make a big difference in security. Stay informed and act quickly to protect yourself.